Depending on the setup you are running sipPROT can be installed in two possible locations:
-
PBXware - in case you are running standalone PBXware installation on dedicated hardware.
-
SERVERware host - If you are running PBXware as a VPS in a SERVERware virtual environment, sipPROT should be installed on all SERVERware hosts.
Brute-force break-in attempts are quite frequent, and VOIP PBX systems that are not protected are susceptible to this attack. The most common consequence of this kind of network attack can be:
- VOIP service downtime and unreachability
- The possibility of password stealing (SIP registration)
This kind of attack on unprotected systems can lead straight to financial loss. To avoid this situation, we developed the sipPROT for PBXware and SERVERware.
sipPROT is protection against brute-force SIP attacks coming from the network.
How does sipPROT work?
When sipPROT detects an attack, it immediately takes action by updating the firewall rules and preventing access from the IP addresses the attack originated from. This keeps your system safe from any further harm. Unlike other similar security solutions, sipPROT is able to work with live SIP traffic and is more effective at stopping attacks.
In addition, sipPROT has a GEO IP blocking feature. This means that it compares incoming IP addresses with a database of GEO IP addresses, and if the incoming IP address is found to belong to a blocked country, sipPROT will automatically block access from that IP. This extra layer of protection ensures that your system is safeguarded from attacks originating from specific geographic locations.
Before you delete any extensions on PBXware, it's important to reset the phone registered on that extension to its factory settings. If you don't, you may end up with many failed "REGISTER" packets, which can cause sipPROT to block the IP addresses associated with those phones. If this happens, you'll receive an email notification at the address you've set under the Notification Recipients tab (assuming your SMTP settings are correct). So, to avoid any issues, make sure you reset the phone to factory settings before deleting any extensions.
¶ Accessing sipPROT in PBXware/SERVERware GUI
- PBXware > Admin settings > sipPROT > Settings, are configuration options for sipPROT.
- SERVERware > Networks > sipPROT.
¶ sipPROT Dashboard
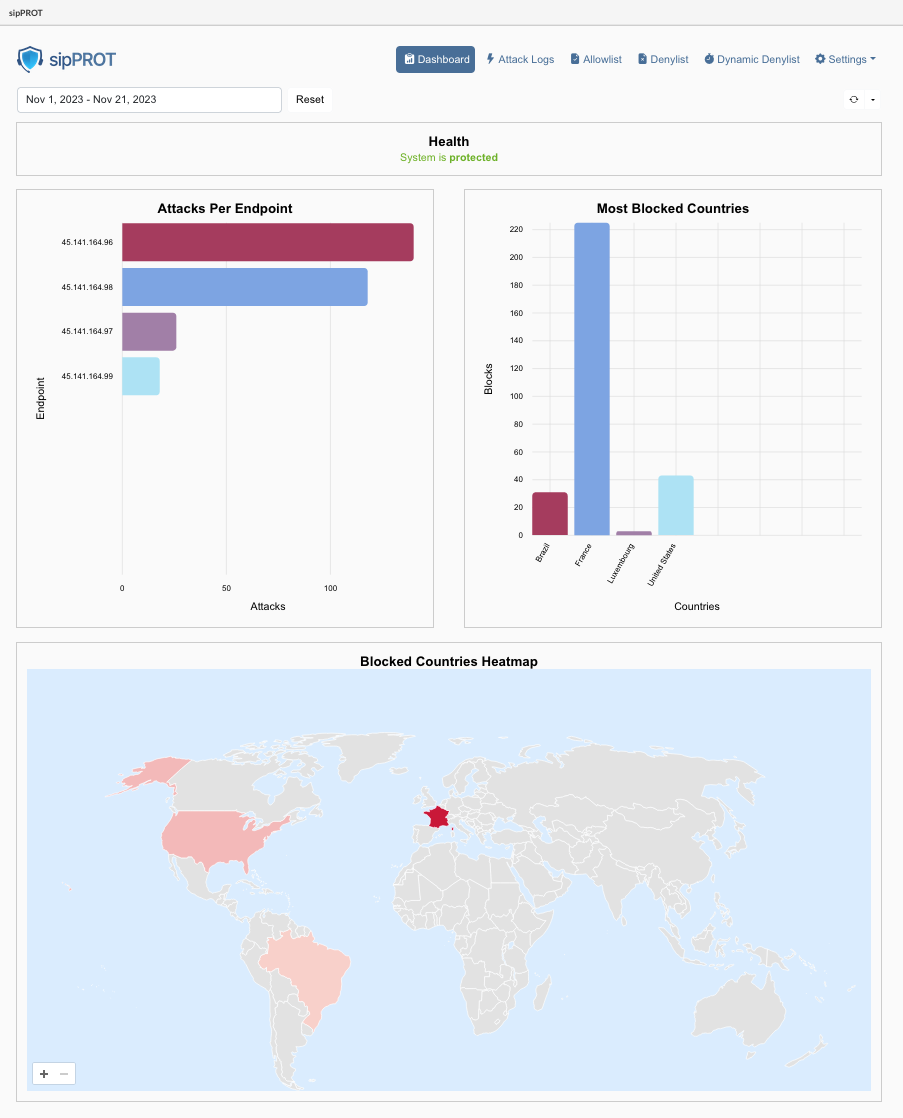
| Widget | Description |
|---|---|
| Health: | This widget displays the health status of the sipPROT service. It indicates whether the service is running smoothly or if there are any issues. If there are problems detected, users are prompted to check the hosts page for more details. A direct link to the hosts page is also provided for quick access. |
| System is protected System did not detect any health issues. | |
| Issues detected: Please check the hosts page via direct link or from the menue to see details. | |
| Attacks Per Endpoint | This widget shows a list of attacks for a specified time period, helping to identify which IP addresses or Virtual Private Servers (VPS) are most targeted on your server. For PBXware users, this will typically show attacks on a consistent IP address. |
| Most Blocked Countries | This widget displays information about the origin countries of blocked IP addresses. It groups blocked IPs based on their country of origin, providing insights into geographic patterns in the attack data. |
| Blocked Countries Heatmap | A geolocation heatmap that visually represents the density or intensity of attacks based on geographic location. It uses color coding to indicate areas with higher and lower concentrations of attacks. Warmer colors indicate higher concentrations of attacks, while cooler colors indicate lower concentrations. |
| All these widgets are affected by the date picker filter and the refresh time selector on the dashboard. This means you can customize the displayed data based on specific time frames and set how frequently the information is updated. | |
| Each widget provides valuable insights into different aspects of the security and health of the system managed by sipPROT, making it easier for users to monitor and respond to potential threats or issues. |
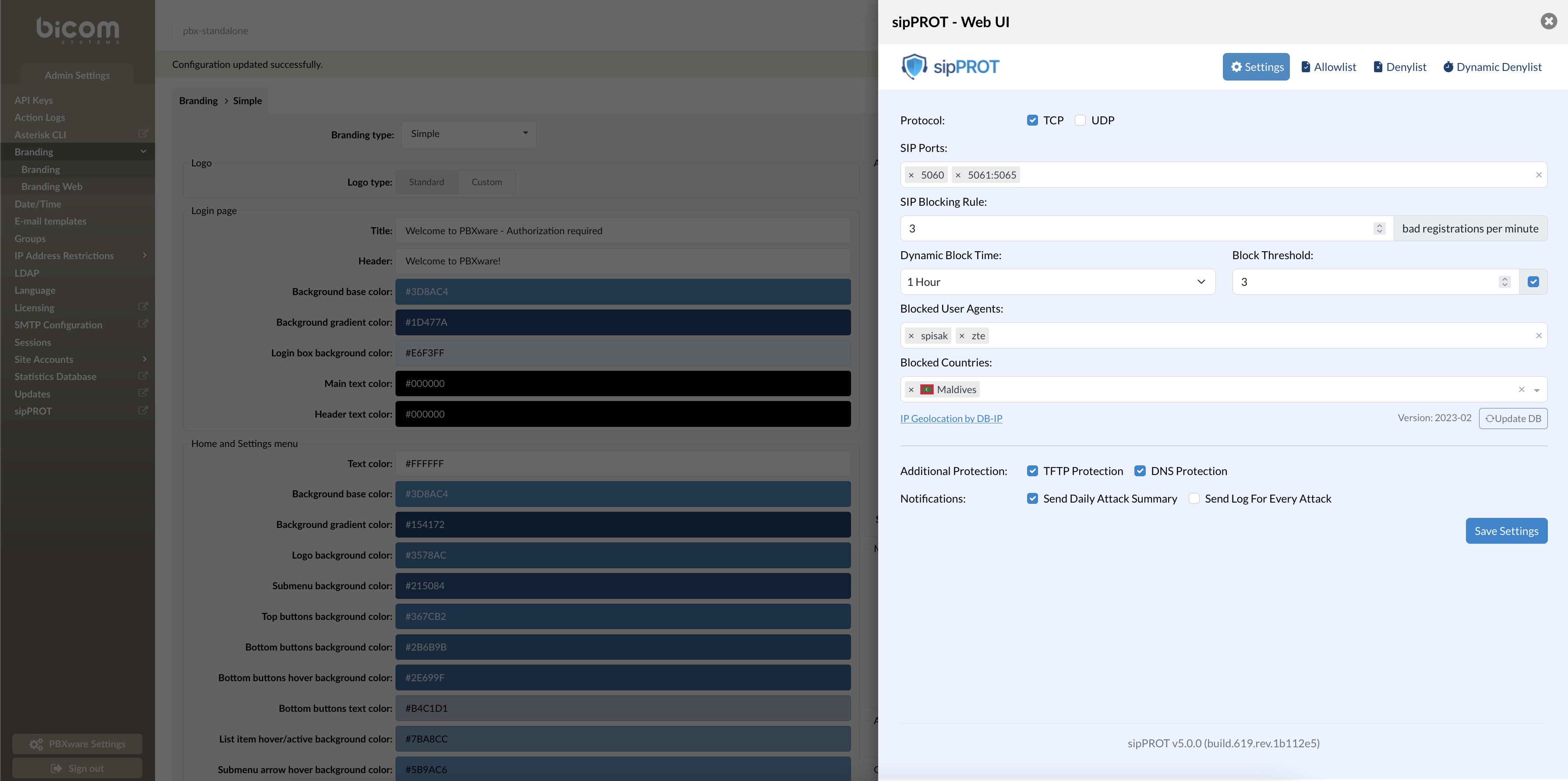
¶ sipPROT Settings
General sipPROT configuration can be found under menue Settings > Firewall.
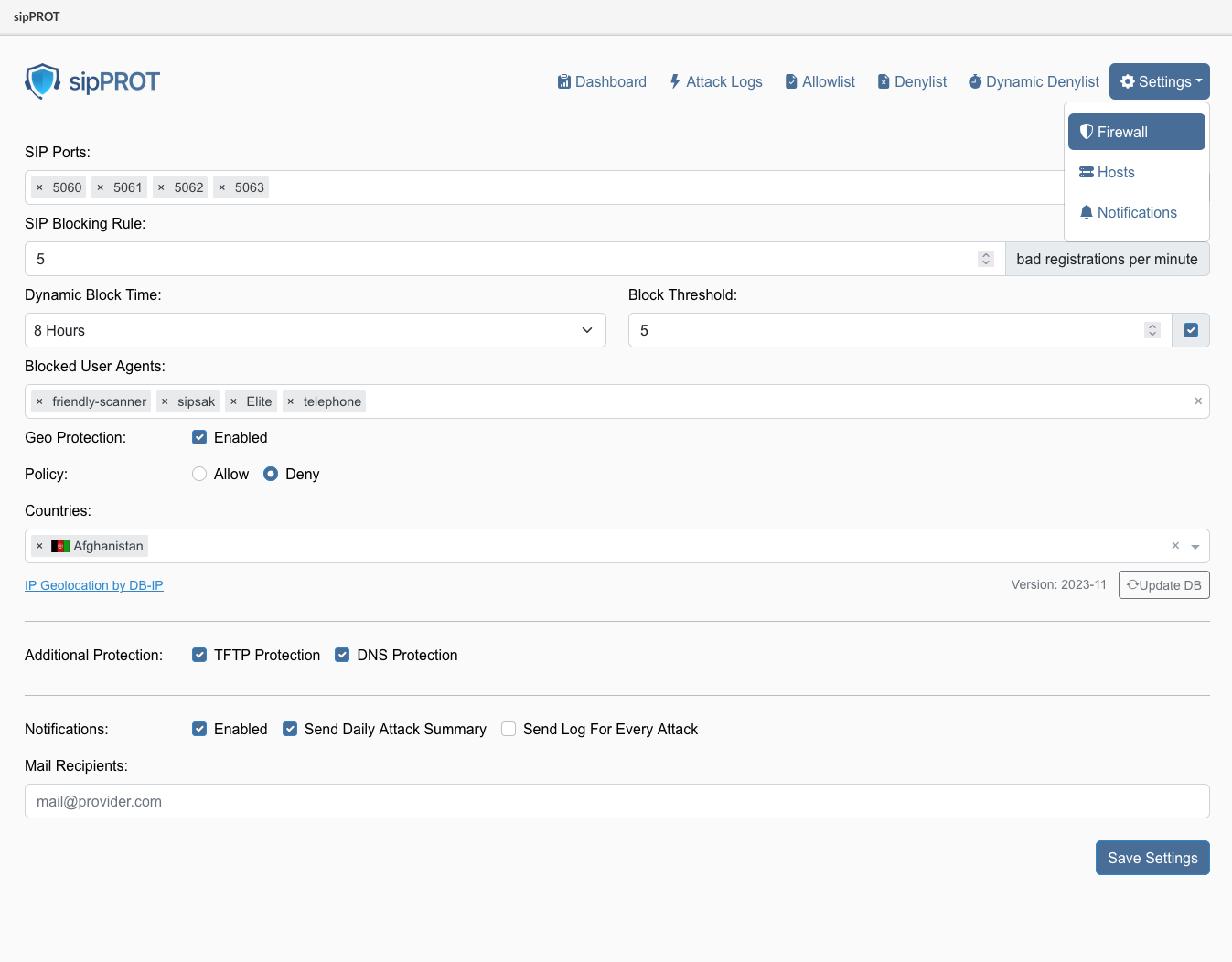
¶ The description for the options available:
| Field | Description |
|---|---|
| SIP Ports: | Specify one or more ports or ranges to monitor, such as "5060" or "5060:5062". |
| SIP Blocking Rule: | Set the maximum number of unauthorized registration attempts per minute before blocking an attacker's IP address for a specified amount of time. |
| Dynamic Block Time: | Choose how long blocked IP addresses will remain blocked after preventing an attack. |
| Block Threshold: | Define how many times an IP address will be dynamically blocked before it is permanently blocked by being added to the denylist. The acceptable range is (1-20). |
| Blocked User Agents: | Specify the SIP user agents to block incoming traffic from. Keep the list as short as possible to avoid affecting system performance. |
| Geo Protection: | Enable or disable GEO blocking, and select either the 'Allow' or 'Deny' option. |
| Allow: If 'Allow' is selected, only traffic from selected countries will be permitted, and all other traffic will be denied. Ensure that resources the server needs to access outside the selected countries, such as email or external archiving servers, are explicitly allowed. | |
| Deny: If 'Deny' is selected, all traffic from the blocked countries will be denied. | |
| Blocked Countries: | Select the countries from which to block incoming traffic. sipPROT will block the entire range of IP addresses belonging to the selected countries, or allow them if a different method is selected above. |
| Additional Protections: | |
| TFTP: Protect your server against TFTP brute force attacks using a rate limit. The default rate limit is 10 requests per minute, with a maximum of 100 burst requests. | |
| DNS: Protect older systems from the glibc stack-based buffer overflow in getaddrinfo() security flaw. If DNS zones are actively in use within SERVERware, it is essential to disable sipPROT DNS protection. Failure to do so may result in conflicts or operational issues. This feature is enabled by default and should not be modified unless you know what it is for. | |
| If you are unsure what the feature is for, you should not modify this option under no circumstances. | |
| Notifications: | |
| Enable: Enable or disable notifications from sipPROT. | |
| Send Daily Attack Summary: Receive an email with a daily report of attacks if this option is ticked. | |
| Send Log For Every Attack Receive a notification for every attack. The default value is once per hour. | |
| Mail recipients: | |
| Enter the email addresses of all intended recipients for sipprot notifications. | |
| The SMTP settings must be correctly configured for email notifications to be sent successfully. | |
¶ Attack Logs
Regularly monitor the attack logs to stay informed about the types and frequencies of attacks your system is facing.
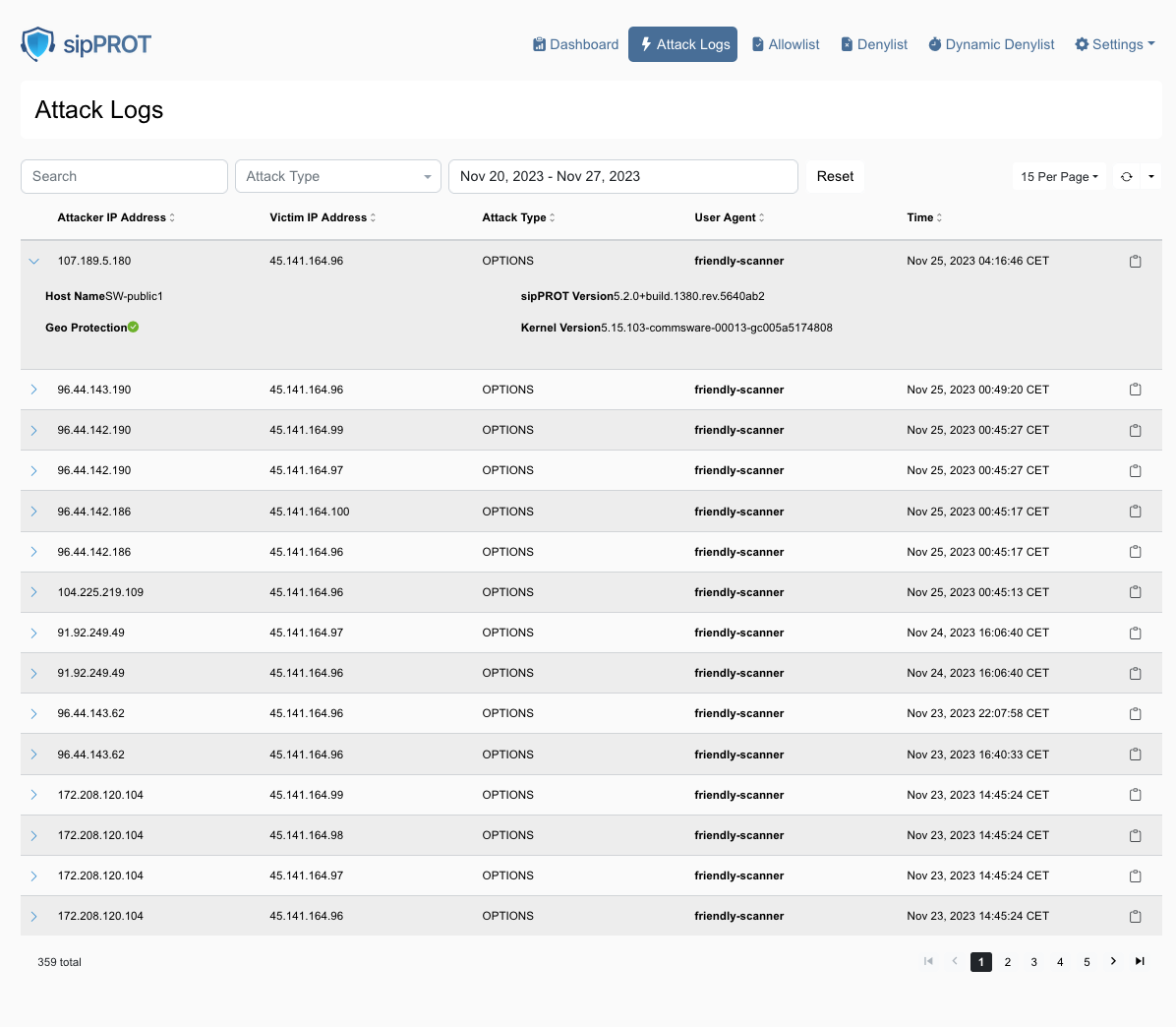
How to Use the sipPROT Attack Logs Page:
| Understanding the Interface: | Attack logs page displays a table of SIP (Session Initiation Protocol) attacks detected by sipPROT. The columns include Attacker IP Address, Victim IP Address, Attack Type, User Agent, and Time of attack. |
| Reviewing Attack Logs: | Scan through the list to review the recent attacks detected by sipPROT. Look at the 'Time' column to see when each attack occurred. The 'User Agent' column may give you insights into the type of tools used for the attack. If the user agent in the list is bold it will indicate that user agent is blocked explicitly in the sipPROT settings. |
| Filtering Logs: | Use the 'Search' bar to filter logs by specific criteria, like IP address or attack type. You can select different types of attacks from the 'Attack Type' dropdown to narrow down the logs displayed.There are two type of attacks available to filter OPTIONS and REGISTER. |
| Inspecting Specific Attacks: | Click on the IP address of either the attacker or victim to possibly see more details about that particular entity (this functionality depends on sipPROT’s features). |
| Managing Logs: | Use the date filter at the top to adjust the range of logs you are viewing. You can reset any filters you have applied by clicking the 'Reset' button. |
| Using Geo Protection: | If available, the 'Geo Protection' indicator can show if geo-blocking features are active or whether an attack was mitigated based on geographical rules. |
| Navigating Pages: | Use the navigation arrows or page numbers at the bottom to scroll through multiple pages of logs. |
| Adjusting View Settings: | You can change how many logs you see per page by adjusting the setting in the top right corner where it says '15 Per Page'. |
| Taking Action: | Based on the information in the logs, you might decide to update your firewall rules, add certain IP addresses to a blocklist, or take other security measures. |
¶ Allow/Deny lists
The Allow/Deny lists offer a variety of management options, such as searching, exporting, importing, and deleting entries. Additionally, users can easily access more detailed information for each entry with a single click, offering valuable insights for more effective list management.
¶ Buttons

- Add (Mannualy add single IP record to the list)
- Export (export the whole list to a CSV file)
- Import (import the list from a CSV file)
- Delete (delete selected IP record)
¶ Search
- Search (Search the list by IP record or note)
- Country (Search IP records by country)
- Reset (Clear the country and reset the search)
¶ Display and refresh options
- Show per page (dropdown to select number of records displayed per parge)
- Refresh (The "Refresh" option in the allow list is a dropdown that allows users to set the refresh interval for the list. When a refresh interval is set, the list will automatically refresh at the specified interval. However, it's important to keep in mind that this action may clear any current selections in the list. )
¶ At the bottom of the list, users can find:

-
Number of selected/total records.
-
Page numbers with selector.
¶ Note
Also for the convinience additional information regarding the specific IP can be found with a single click on the arrow on the beggining of the record to expand the additional information for the record, containing:
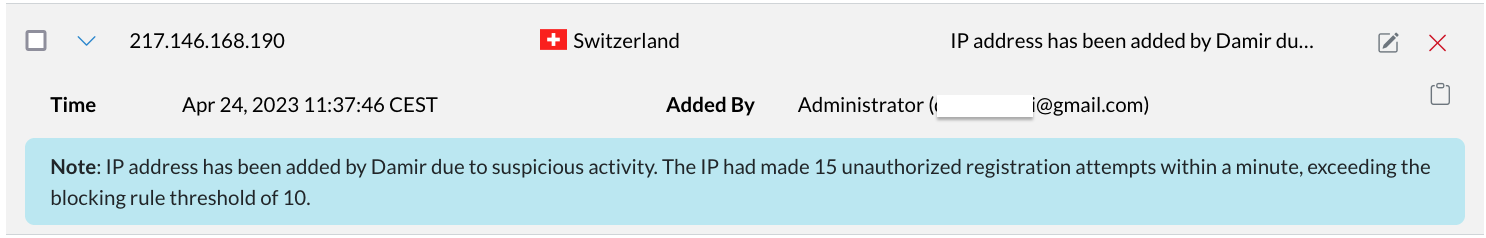
- Note: the note for the record if available.
- Added By: the user who added the record.
- Copy button: copy the record data in the clipboard in json format.
{
"ip": "217.146.168.190",
"note": "IP address has been added by Damir due to suspicious activity. The IP had made 15 unauthorized registration attempts within a minute, exceeding the blocking rule threshold of 10.",
"time": 1682329066,
"added_by": "Administrator (user@gmail.com)",
"geo_data": {
"country_code": "CH",
"country_name": "Switzerland"
}
}
- Edi: edit the record button.
- Delete: delete the record button.
¶ Allowlist
The allowlist is a list of IP addresses that are allowed uninterrupted access to the system. This list can be manually populated via a form or uploaded using a CSV file. It is important to keep the allowlist up-to-date to ensure that legitimate users are not blocked from accessing the system.
The allowlist provides an additional layer of security to the system and helps prevent unauthorized access.
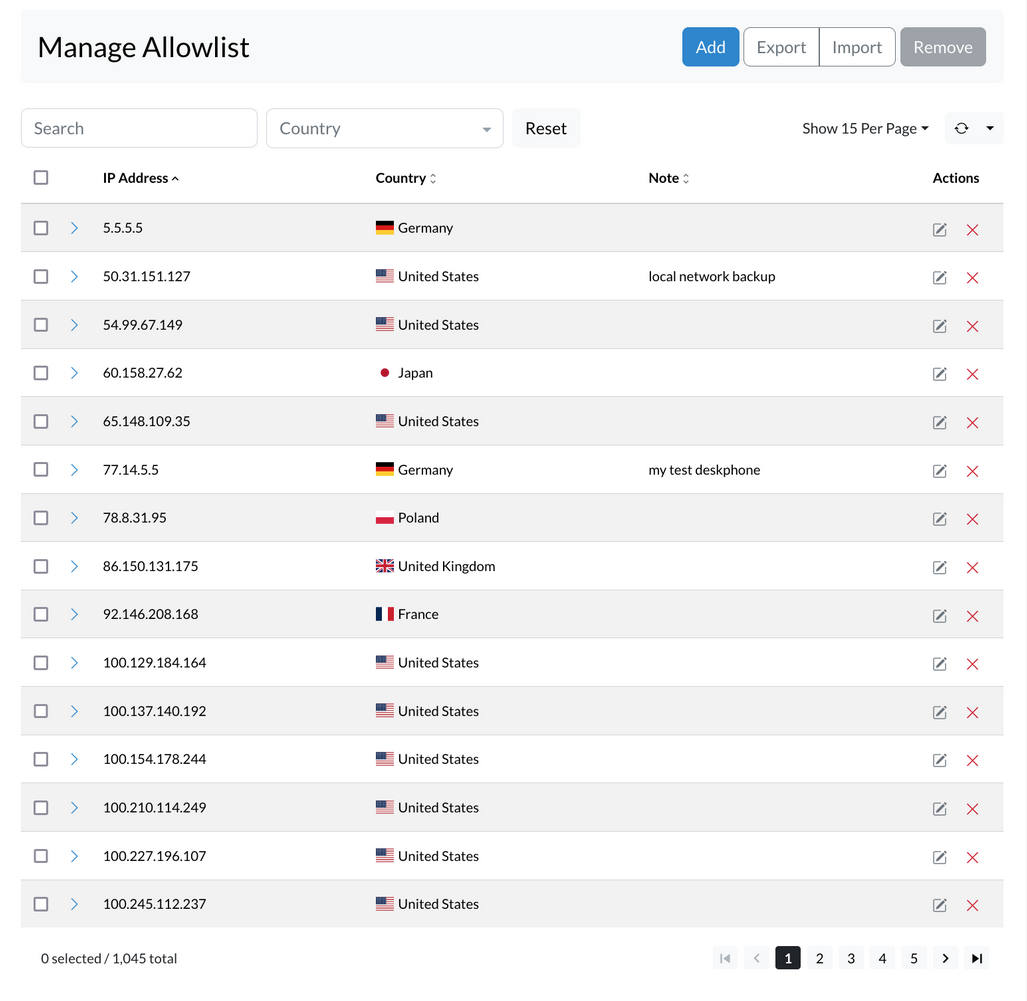
¶ ADD IP records to Allowlist
To add an IP address to the Allowlist, follow these steps:
- Open the Allowlist sipPROT tab in your system.
- Click on the "ADD" button.
- Enter the Network or IP address in the designated field.
- Enter any optional notes to help you remember why this address was added.
- Click the "Add" button to add the IP address to the Allowlist.
It's important to ensure that the entered IP address is accurate and valid. Once an IP address is added to the Allowlist, it will be allowed uninterrupted access to the system.
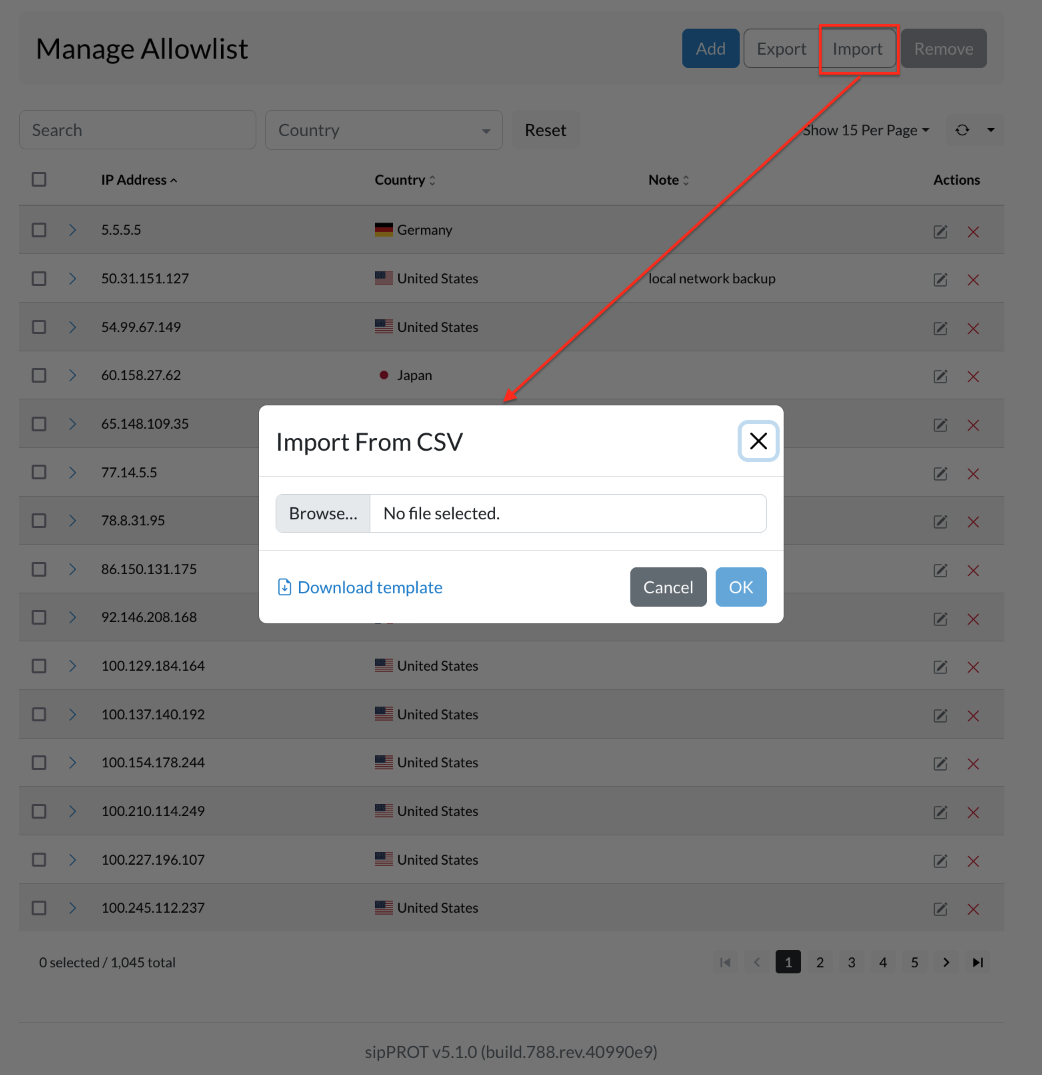
¶ IMPORT / EXPORT Multiple IP records to Allowlist
To import multiple IP addresses into the Allowlist, you can use the Import CSV option located in the upper right corner of the Allowlist IP Addresses tab. To use this feature, you will need to have a CSV file that contains the list of IP addresses you wish to add to the Allowlist.
To create the CSV file, you can download the provided template file that contains headers and examples to help you get started. Once you have the file, open it in a spreadsheet program like Microsoft Excel or Google Sheets. Then, add the IP addresses you want to allow access to the system under the "IP_ADDRESS" column. You can also add an optional note for each IP address in the "NOTE" column.
Example CSV file :
IP_ADDRESS,NOTE
192.168.x.x,"example note1"
77.14.x.x,"example note2"
Save the file as a CSV and make sure it is in the correct format. Then, go back to the Allowlist sipPROT tab in the system and click on the "Upload" button. Select the CSV file you just created and click on "Upload" again. The system will import the IP addresses from the file and add them to the Allowlist.
If you need to export the list of IP addresses from the Allowlist, you can also use the "Export CSV" option to download a file that contains all of the IP addresses currently on the Allowlist.
¶ Remove IP address from the list
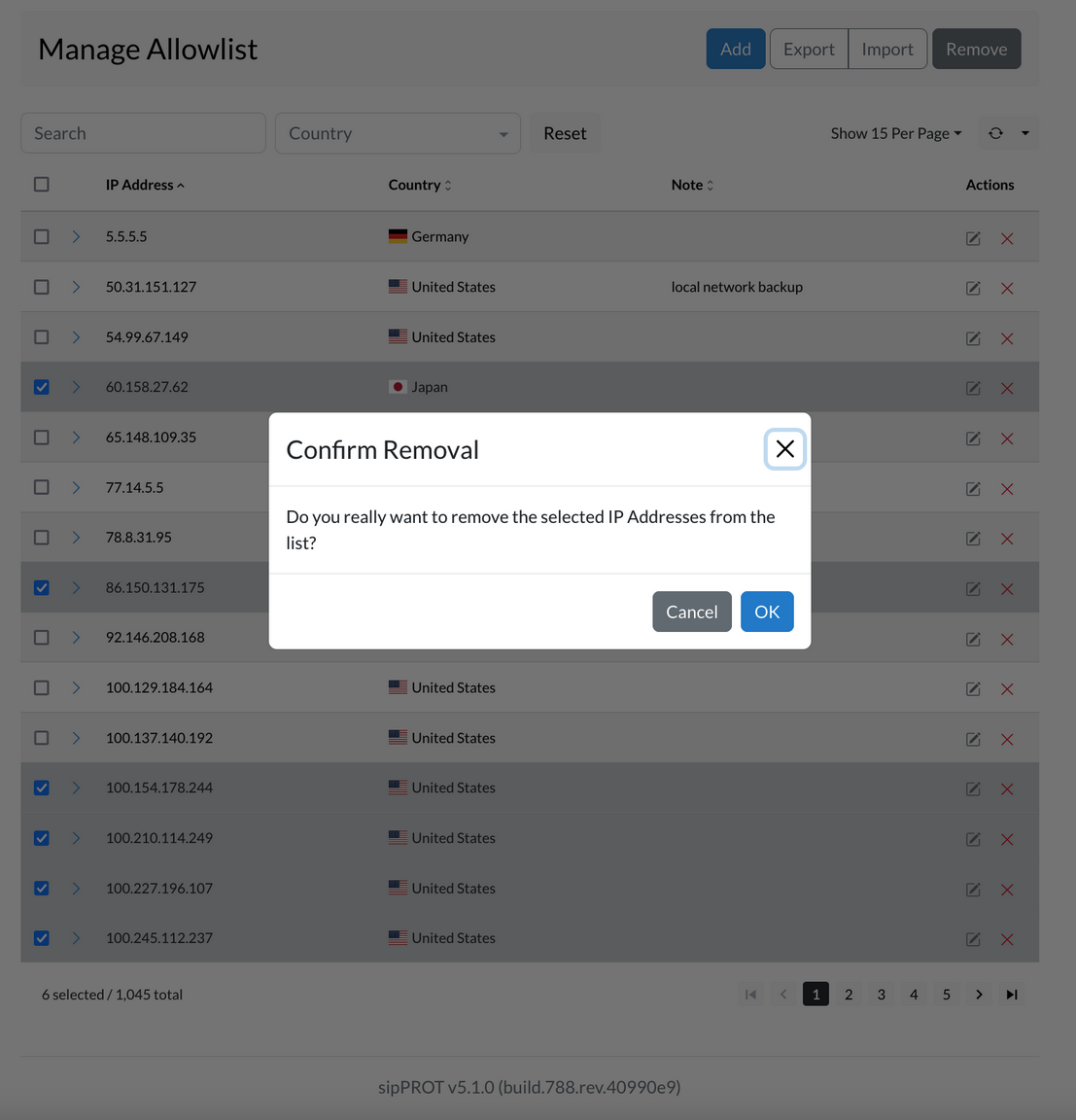
There are two ways to remove a network or IP address from the list. First, you can select one or multiple IP addresses by checking the box next to each one, then clicking on the "Remove" button. A confirmation dialog will appear, and you can click "Yes" to remove the selected network or IP addresses.
Secondly, you can remove all IP addresses from the list by clicking the "Select all" checkbox, then clicking the "Remove" button. A confirmation dialog will appear, and you can click "Yes" to remove all network or IP addresses from the list.
Changes made to the list are applied automatically. If you need to remove a large number of IP addresses, you can also use a CSV file to make bulk changes. A link to a template file with headers and examples is provided to help you get started.
The Allowlist takes precedence over other lists. If an IP address is present in both the Allowlist and a different list (such as the Denylist), the IP address will still be granted access to the system, and the other list will be ignored.
This can be useful when blocking a network or range of IPs (such as "192.168.50.0/24") but needing to allow access for a specific IP address within that range (such as "192.168.50.15"). By adding the allowed IP address to the Allowlist, it will be granted access to the system despite the broader network block in the Denylist.
¶ Denylist
The Denylist is a collection of IP addresses that have restricted access to the system. This list can be populated manually by entering an IP address and an optional "note" through a GUI or by importing a list of IP addresses via a CSV file. Additionally, the Denylist can be dynamically populated with IP addresses from the Dynamic Denylist if they are identified as being associated with persistent attacks on the system.
IMPORTANT - The Allowlist has precedence over the Denylist. If an IP address is present in both the Allowlist and the Denylist, the IP address will be granted access to the system.
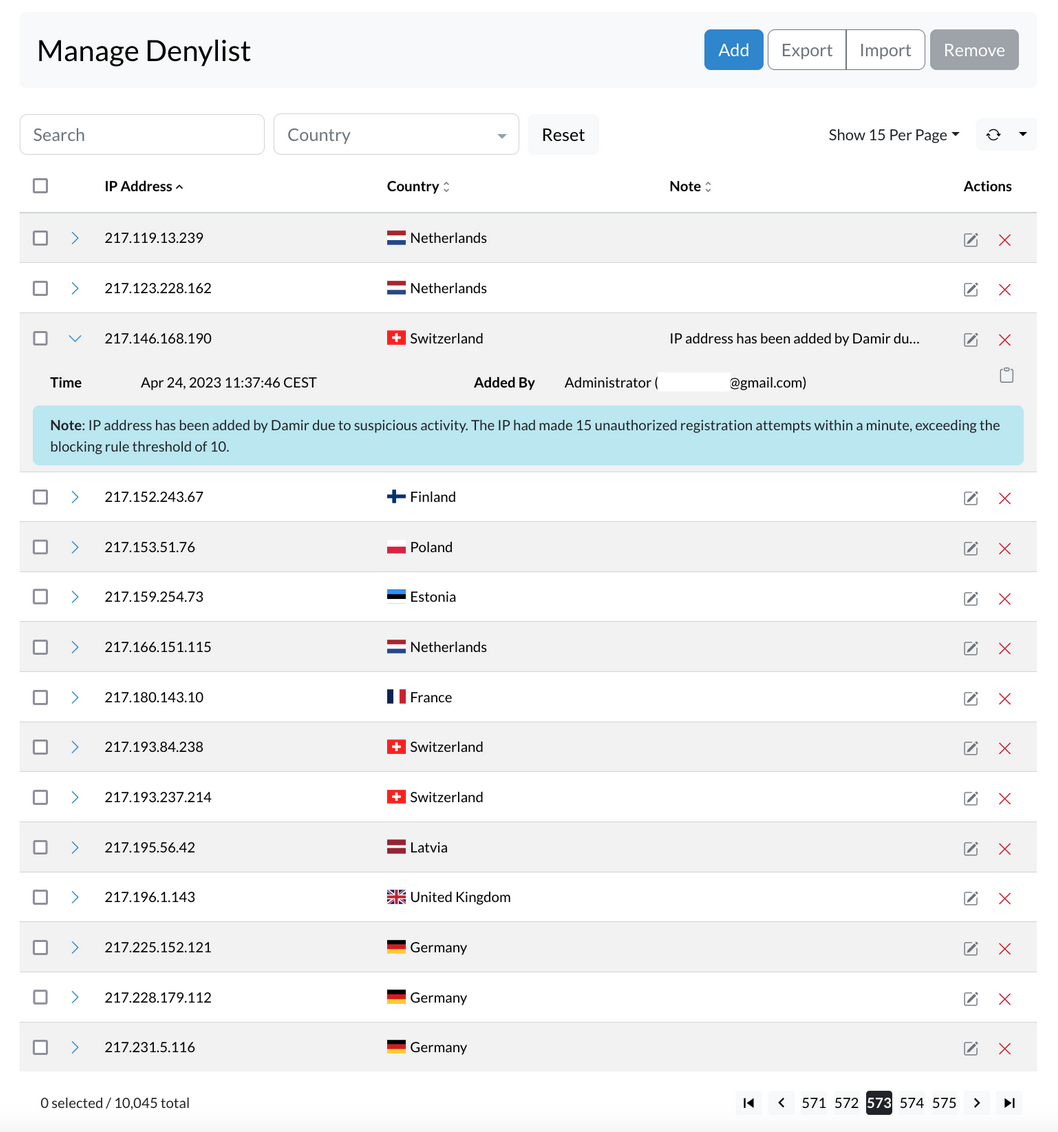
¶ ADD IP records to Denylist
To add an IP address to the denylist, follow these steps:
- Open the Denylist sipPROT tab in your system.
- Click on the "ADD" button.
- Enter the Network or IP address in the designated field.
- Enter any optional notes to help you remember why this address was added.
- Click the "Add" button to add the IP address to the Denylist.
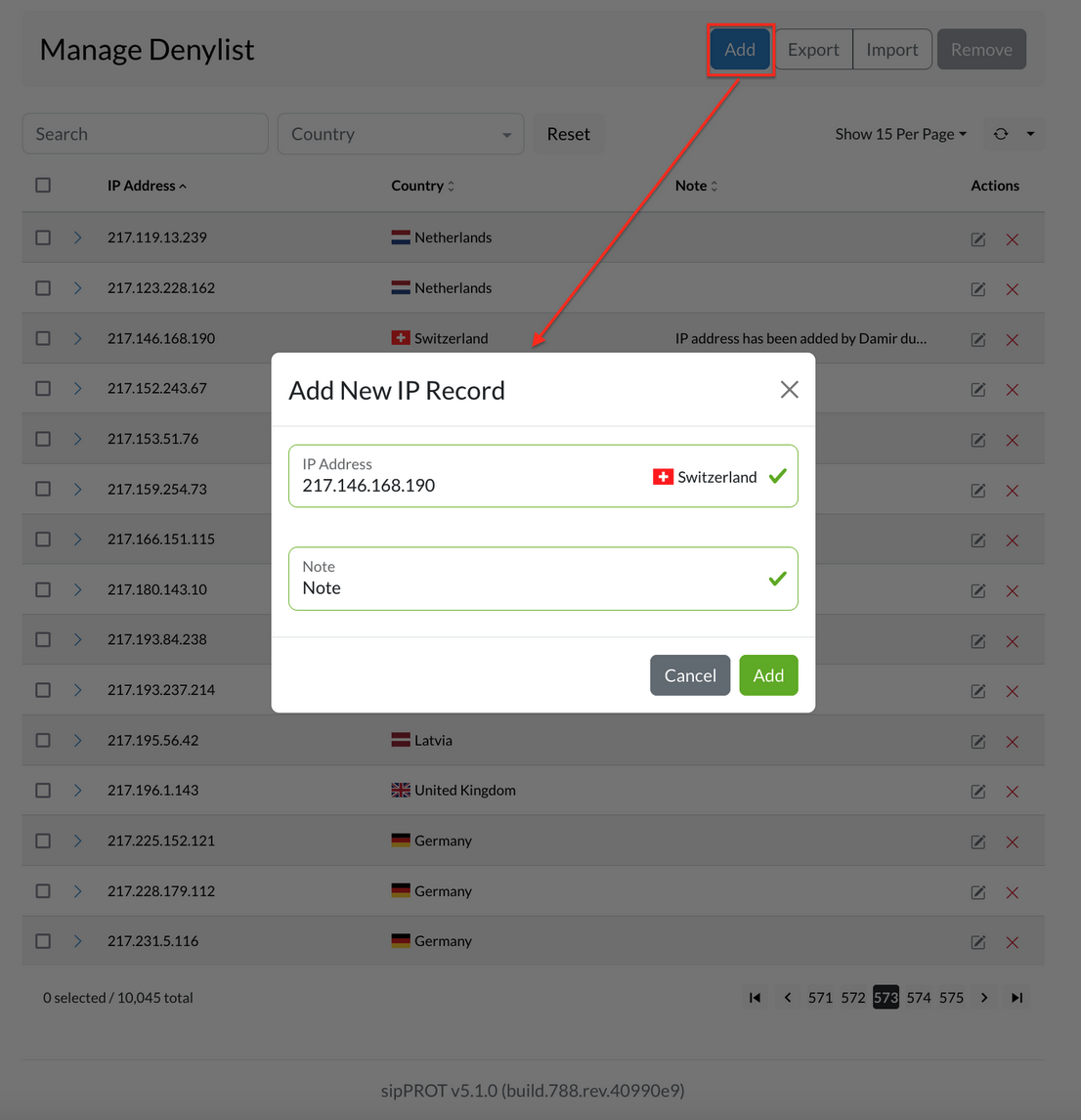
¶ IMPORT / EXPORT Multiple IP records to Denylist
To import multiple IP addresses into the Denylist, you can use the Import CSV option located in the upper right corner of the Denylist tab. To use this feature, you will need to have a CSV file that contains the list of IP addresses you wish to add to the Denylist.
To create the CSV file, you can download the provided template file that contains headers and examples to help you get started. Once you have the file, open it in a spreadsheet program like Microsoft Excel or Google Sheets. Then, add the IP addresses you want to allow access to the system under the "IP_ADDRESS" column. You can also add an optional note for each IP address in the "NOTE" column.
Example CSV file :
IP_ADDRESS,NOTE
192.168.x.x,"example note1"
77.14.x.x,"example note2"
Save the file as a CSV and make sure it is in the correct format. Then, go back to the Denylist sipPROT tab in the system and click on the "Upload" button. Select the CSV file you just created and click on "Upload" again. The system will import the IP addresses from the file and add them to the Denylist.
If you need to export the list of IP addresses from the Denylist, you can also use the "Export CSV" option to download a file that contains all of the IP addresses currently on the Denylist.
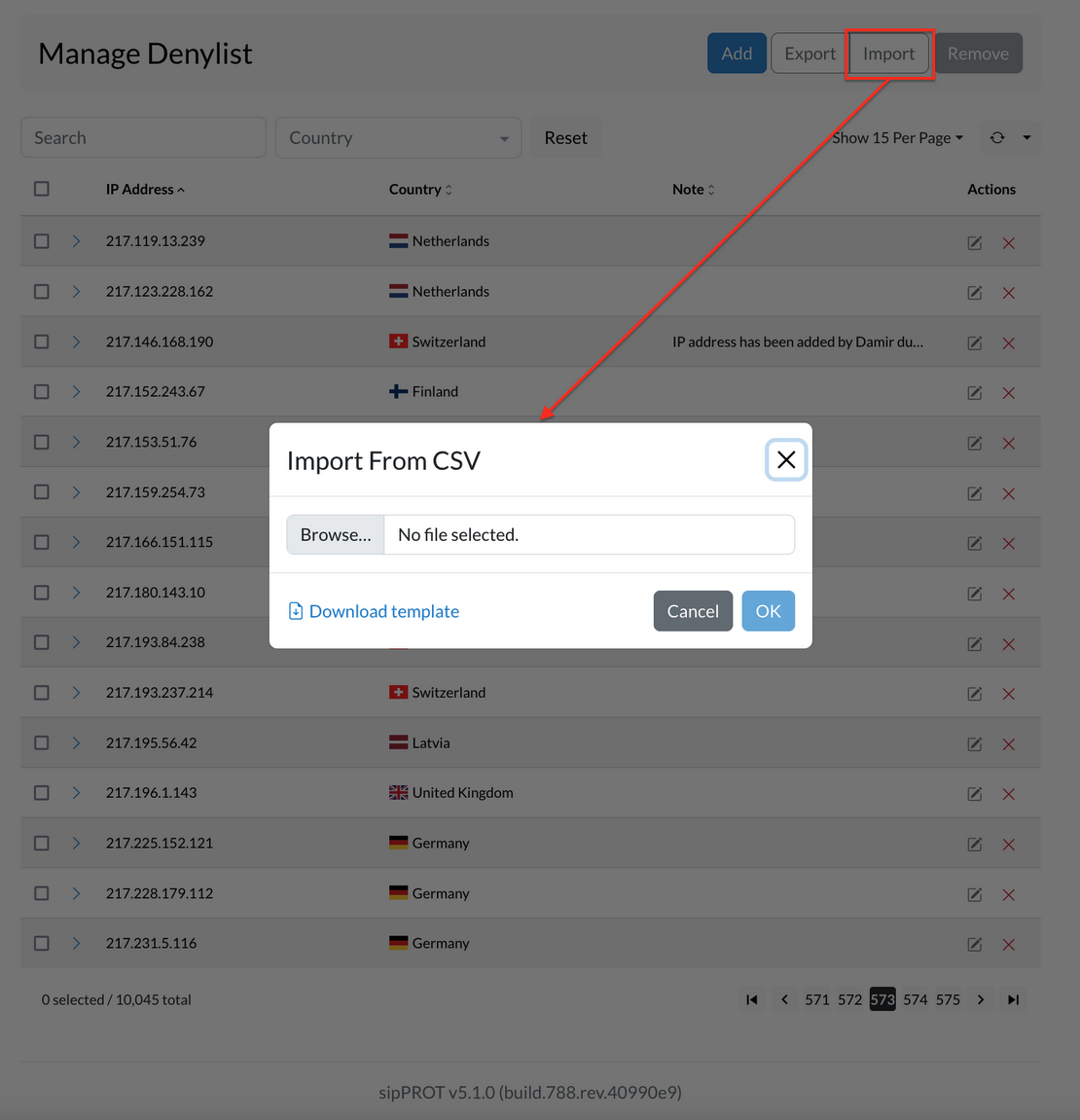
¶ Remove IP address from the list
There are two ways to remove a network or IP address from the list. First, you can select one or multiple IP addresses by checking the box next to each one, then clicking on the "Remove" button. A confirmation dialog will appear, and you can click "Yes" to remove the selected network or IP addresses.
Secondly, you can remove all IP addresses from the list by clicking the "Select all" checkbox, then clicking the "Remove" button. A confirmation dialog will appear, and you can click "Yes" to remove all network or IP addresses from the list.
Changes made to the list are applied automatically. If you need to remove a large number of IP addresses, you can also use a CSV file to make bulk changes. A link to a template file with headers and examples is provided to help you get started.
¶ Dynamic denylist
The Dynamic Denylist display automatically blocked IP addresses that are identified as sources of malicious traffic or attacks. These IP addresses are added to the Denylist automatically without any manual intervention. The Dynamic Denylist is constantly updated with the latest information on malicious IP addresses, ensuring that the system remains protected against new threats.
Administrators have the option to manually unblock the IP address or wait for the timeout period to expire, at which point the block will be automatically removed.
One of the advantages of the Dynamic Denylist is that it provides detailed information on the user agent/scanner used in the attack, as well as the country of origin of the attack. This information can be used for inspection and debugging purposes, as well as to better understand the nature of the attack and take appropriate measures to prevent future attacks.
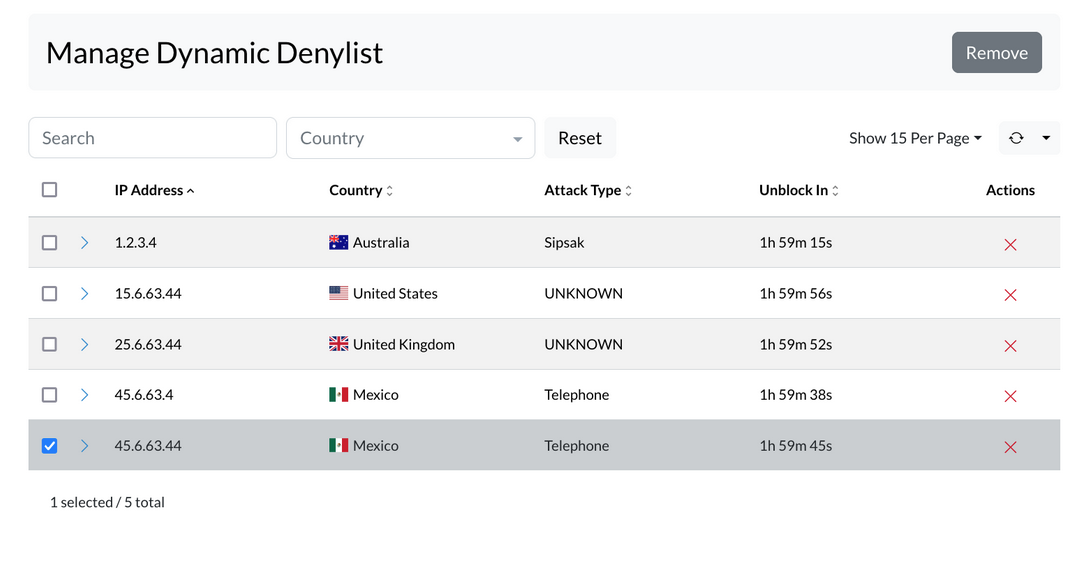
Dynamic deny is a security feature in sipPROT designed to automatically block IP addresses that exhibit malicious behavior against your system. This feature operates based on a set of predefined rules established by the administrator. Here's a more detailed explanation:
| Field | Description |
|---|---|
| Dynamic Blocking: | When an IP address attempts an action that violates the rules set in sipPROT (like repeated failed login attempts, which could indicate a brute force attack), the dynamic deny feature is triggered. This results in the offending IP address being temporarily blocked. |
| Dynamic Block Time: | This is a crucial setting within the dynamic deny feature. It specifies the duration for which an IP address will be blocked once it violates the rules. For example, if the Dynamic Block Time is set to one hour, any IP address that breaks the rules will be blocked for an hour. |
| Behavior During the Block Period: | If the blocked IP address attempts another attack while it is still in the blocked state, the Dynamic Block Time is reset. This means the block duration starts over, and the IP remains blocked for another full hour from the time of the new attack. |
| Unblocking: | If the blocked IP address does not attempt any new attacks during the block period, it will be automatically unblocked once the Dynamic Block Time elapses. |
| Permanent blocking: | An IP address is added to the denylist if it persistently attacks and is repeatedly blocked by the dynamic deny feature. This is governed by the "Block Threshold" setting. For example, if an IP address commits more than 3 attacks within a specified time frame (as defined in your settings), it will be permanently blocked, meaning it is moved to the denylist. This ensures that consistently malicious sources are dealt with more stringently. |
In essence, the dynamic deny feature in sipPROT is a proactive security measure that automatically imposes temporary blocks on IP addresses that exhibit potentially harmful behavior, based on the rules configured by the system administrator. This helps in protecting your system from ongoing and repeated attacks while allowing for automatic unblocking in cases where the threat may no longer be present.
¶ sipPROT Hosts
To access the hosts page use the top navigation menu Settings > Hosts, or click directly on the dasboard, Health widget.
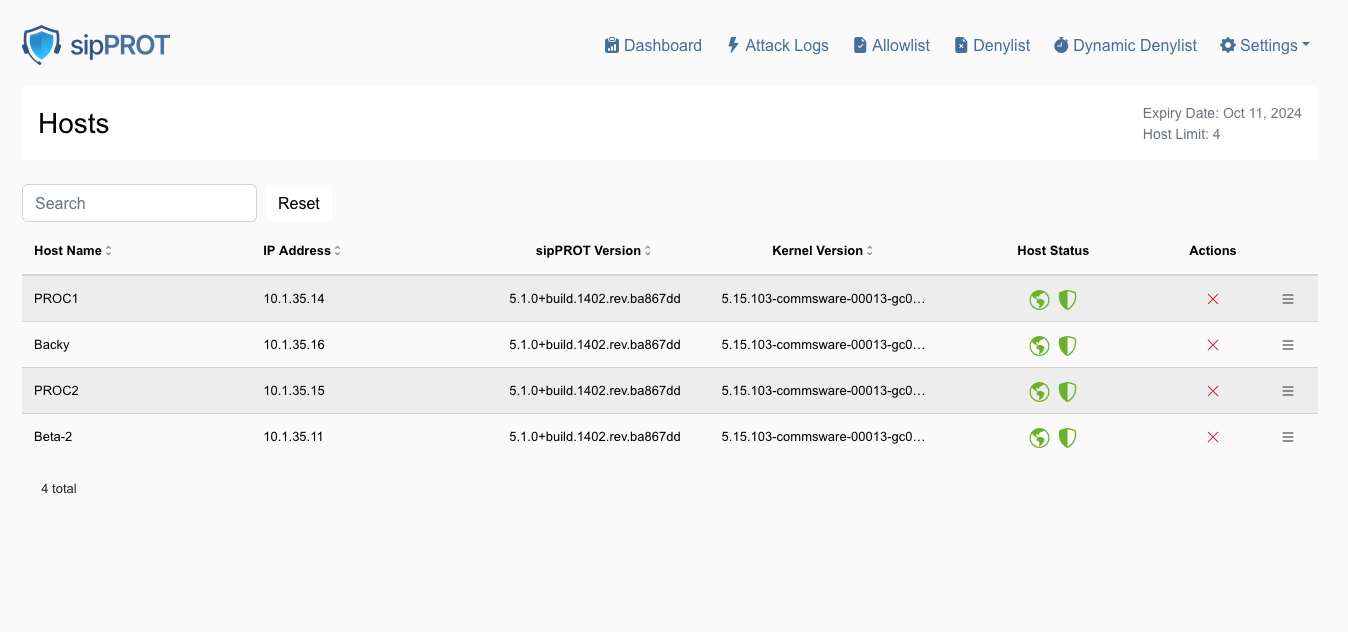
This includes:
| Service Status Per Host: | Displays the current operational status of the sipPROT service on individual hosts. Red shield icon is a sign that service on the host is not running and need to be inspected. |
| License Information: | Shows details about the sipPROT license, such as its validity and the number of hosts it covers. |
| GEO Protection Status: | Indicates whether geo-protection features are active and functioning correctly on each host. Red earth icon is a sign that GEO service on the host is not available and need to be inspected. |
| sipPROT version: | Installed sipPROT version per host. |
| Host kernel version: | Version of the kernel installed per host. |
| Host IP: | Host IP address |
| Additionally, this page provides the functionality to remove hosts. Removing a host from this page will temporarily disable the sipPROT service on that host until it is restarted. This feature is particularly useful in scenarios where there are more hosts than the license permits. For example, backup hosts, which typically do not run SIP services, can be selectively unprotected to stay within the license limits. |
¶ sipPROT Notifications
To access the notifications page in sipPROT use the top navigation menu Settings > Notifications.
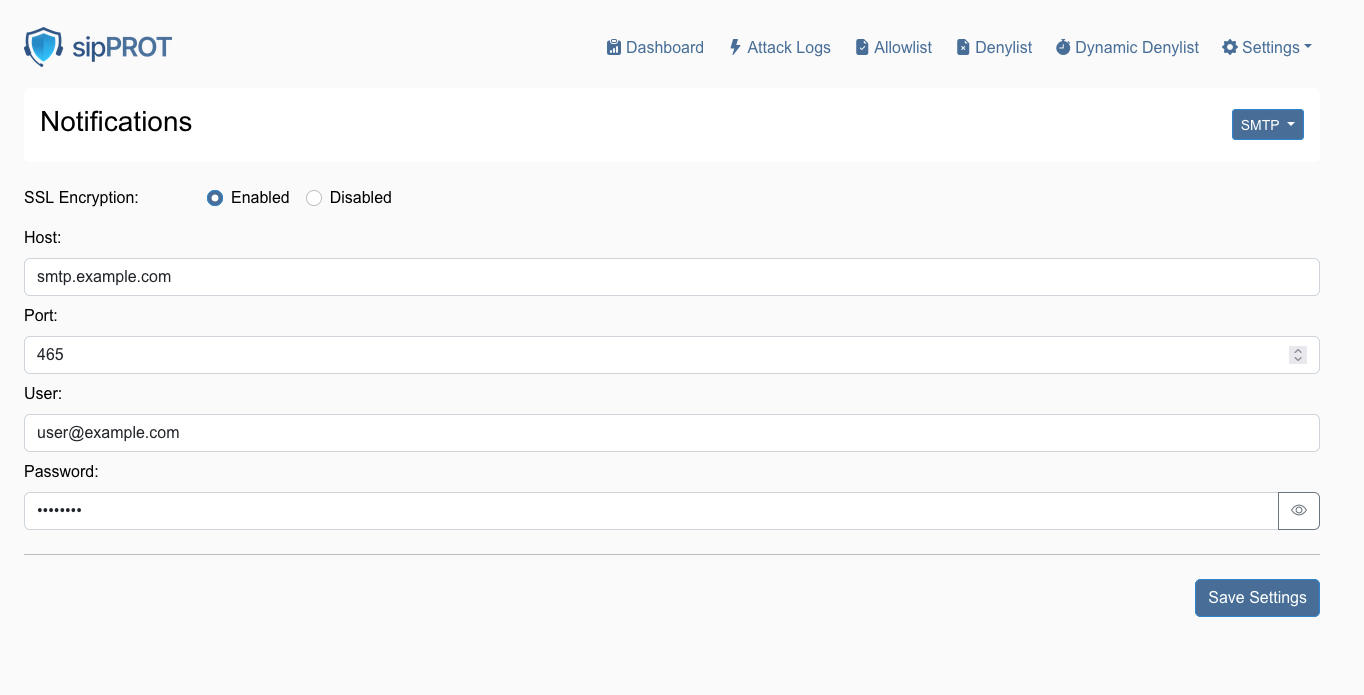
| Configure SSL Encryption: | 'SSL Encryption' option. Select 'Enabled' to ensure that your notification emails are sent using a secure connection. |
| Enter SMTP Details: | |
| Host: | Enter the SMTP server address for your email provider. For example, smtp.example.com. |
| Port: | Input the port number used by your SMTP server. Commonly, this is 465 for SSL or 587 for TLS. |
| Enter User Credentials: | |
| User: | Input the full email address that will be used to send notifications, such as user@example.com. |
| Password: | Enter the password associated with the email account. Make sure to input this accurately. |
| Save Your Settings: | After ensuring all the information is correct, click the 'Save Settings' button to apply the changes. |
¶ sipPROT Branding
sipPROT installed in PBXware will use PBXware branding and language options.
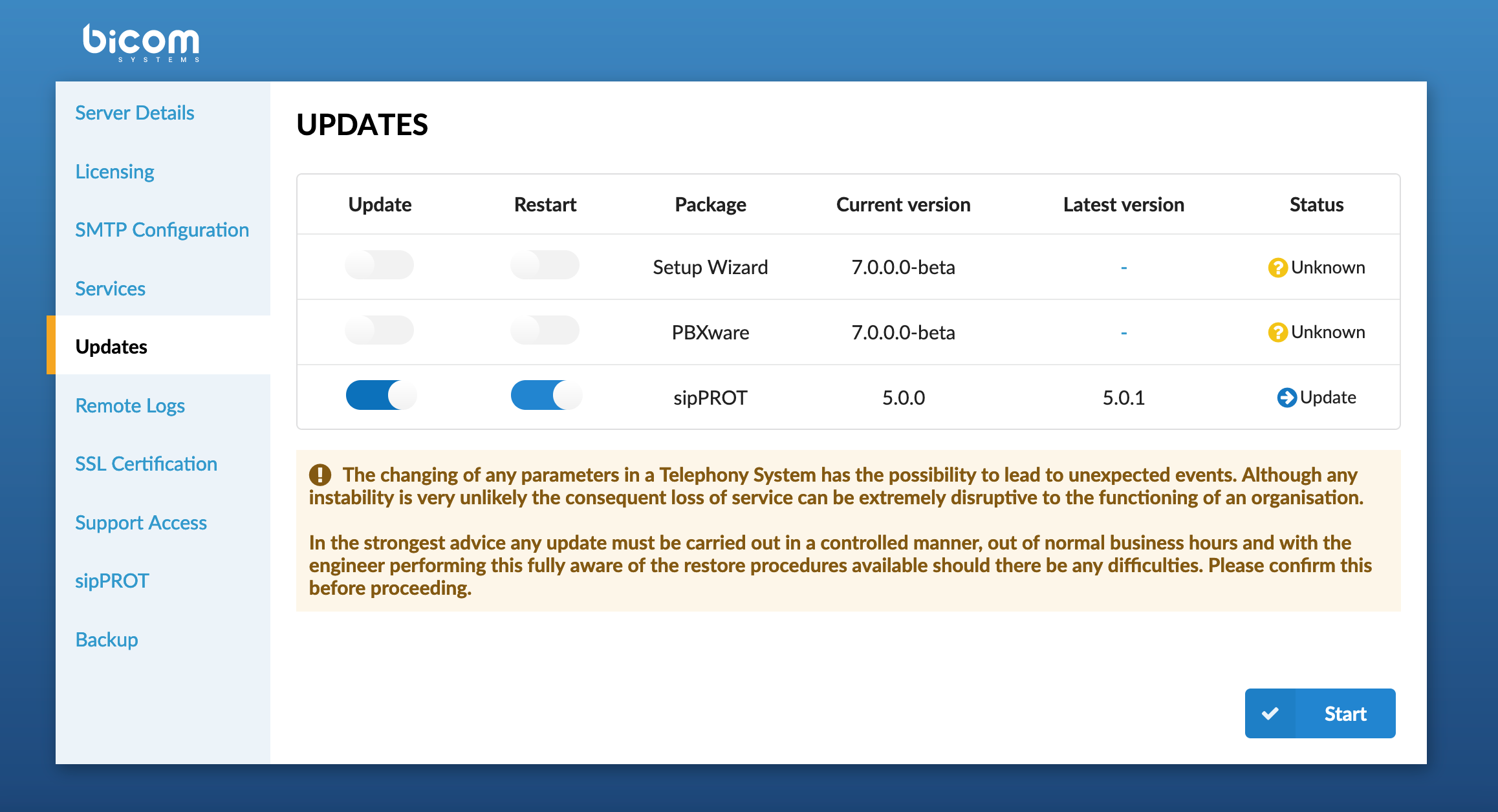
¶ Update sipPROT on PBXware
The sipPROT update can be done from the PBXware setup wizard in the same manner as other PBXware packages.
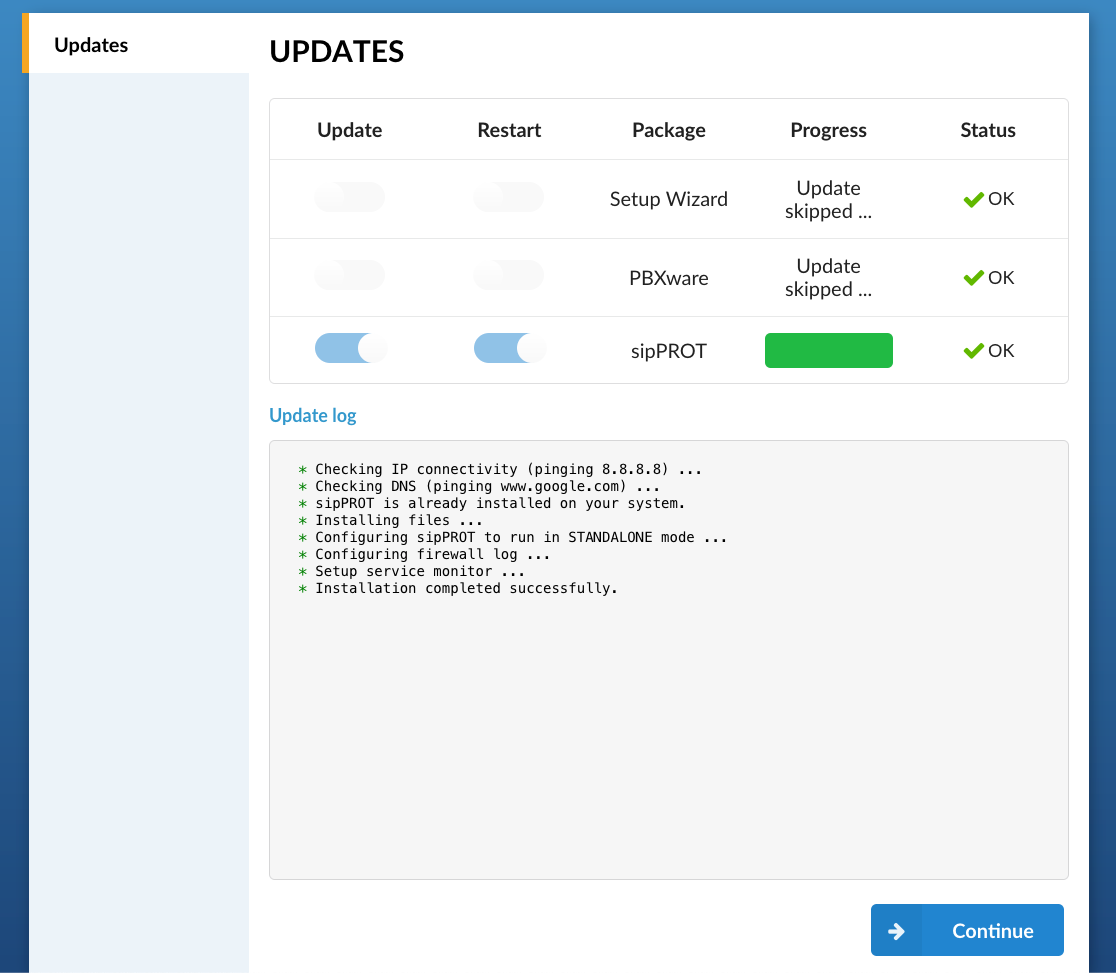
¶ Working with sipPROT CLI
The new updated version of sipPROT comes with updated CLI commands and outputs. CLI autocomplete is added for sipPROT commands.
# sipprot --help
NAME:
sipPROT - CLI
USAGE:
sipPROT [global options] command [command options] [arguments...]
VERSION:
5.1.0+build.1445.rev.2accad6
COMMANDS:
status, s Prints number of IPs per list
check-update, u Check for updates
version, Print only the version
list, l Manages IP lists
settings To inspect settings
help, h Shows a list of commands or help for one command
GLOBAL OPTIONS:
--config FILE load configuration from FILE (default: "/opt/sipprot/conf/sipprot.conf")
--log value log URI e.g. stdout://, syslog:// or file:///var/log/sipprotd.log (default: "stdout://")
--debug include debug logs (default: false)
--help, -h show help
--version, -v print the version
¶ sipPROT status
To get information about sipPROT status use the following command:
- sipprot status
This command will give the following information:
# sipprot status
+---------------------+------------+
| LIST | NUM OF IPS |
+---------------------+------------+
| Allow | 493 |
+---------------------+------------+
| Deny | 482 |
+---------------------+------------+
| Dynamic (temporary) | 100 |
+---------------------+------------+
To list detailed information use flags --all, --allow, --deny, --dynamic
Example:
# sipprot status -allow
Allowlist:
+-----------------+----------------+
| IP ADDRESS | COUNTRY |
+-----------------+----------------+
| 191.85.106.233 | Argentina |
+-----------------+----------------+
| 165.191.222.98 | Australia |
+-----------------+----------------+
| 175.35.61.159 | Australia |
+-----------------+----------------+
| 83.164.34.163 | Austria |
+-----------------+----------------+
| 178.127.91.72 | Belarus |
+-----------------+----------------+
| 178.116.223.166 | Belgium |
+-----------------+----------------+
| 109.140.180.239 | Belgium |
+-----------------+----------------+
Print sipPROT version information:
# sipprot version
sipPROT: 5.1.0+build.777.rev.5ad785a
Additional quick check, if the provided IP is in any of the following: allowlist, denylist, dynamic denylist.
Example:
# sipprot list check 83.221.171.193
IP address '83.221.171.193' found in Allowlist
IP address '83.221.171.193' found in Denylist
"The information shown in the screenshots on this wiki such as IP addresses, hostnames, email addresses, and service versions are placeholders used for demonstration purposes within the sipPROT interface. They are not indicative of actual threats or real-world configuration and should not be treated as such."